Cybersecurity is crucial for any industry. Today most countries have their own data privacy regulations that you have no choice but to comply with. In the modern globalized world, things are even trickier: you may be a legal entity of country A, mostly operate in country B but have most customers from country C.
GDPR, PIPEDA, and HIPAA are a few big names in this field so you’re likely a subject to some or even all of them if you operate within European or North American markets.
In this article, we’ll help you define whether you should comply with these regulations and what it actually means to be HIPAA-, PIPEDA- and GDPR-compliant.
✅ How to Define Whether You Must Comply with GDPR, PIPEDA, and HIPAA?
Let’s start by finding out who is subject to these regulations and whether your mobile application or website must comply with them.
GDPR
TL;DR |
The General Data Protection Regulation (GDPR) is a key data and privacy law from the EU. Yet, taking into account its global impact, the GDPR is definitely one of the top regulations in this field that you can’t help but consider.
The GDPR applies to individuals and companies (including websites and mobile apps, of course) that process personal data of EU citizens.
What’s more: it doesn’t matter whether your company operates from within or outside of the EU, or has any presence in the EU — the GDPR still applies.
Detailed info on this matter can be found in Chapter 1 of GDPR.
PIPEDA
TL;DR |
PIPEDA is a Canadian law that establishes a data privacy framework organizations should comply with. Thus, the regulation applies to Canadian private sector organizations that collect, disclose, or use personal information for commercial purposes.
PIPEDA defines a commercial activity as any particular act, conduct, or transaction that’s of a commercial character: bartering, selling, leasing of donor, membership plans, etc.
What about mobile apps and websites? According to the Office of the Privacy Commissioner of Canada, gathering, disclosing, and using personal information to improve user experience — and that indirectly contributes to the commercial success of the website or application — can still be recognized as a commercial activity.
{ rel="nofollow" .default-md}*)](https://cdn.sanity.io/images/ordgikwe/production/f25de7abde3025b9779f2be97103f62f70c32a73-1200x900.jpg?w=1200&h=900&auto=format)
PIPEDA is one of the key data privacy regulations (image by Matt Anderson)
Unlike GDPR, the Canadian regulation doesn’t specifically mention foreign companies, some of them got penalties in the past. It means that foreign companies also must comply with PIPEDA if they’re collecting, using, or disclosing personal data of Canadian users.
Non-profit organizations as well as educational and healthcare institutions are outside of the PIPEDA’s jurisdiction as long as they aren’t engaged in any commercial activities.
Finally, organizations that operate strictly within provinces of Quebec, Alberta, and British Columbia have to comply with the local privacy laws that are quite similar to PIPEDA. At the same time, such organizations are generally exempt from PIPEDA itself.
HIPAA
TL;DR |
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal U.S. law that introduces national standards to protect personal health data, which is particularly relevant when you build a medical app. The law sets a number of criteria to define covered entities and business associates that must comply with the regulation.
A covered entity is one of the following:
🏥 Health сare Provider* | 📋 Health Plan | 🔄 Health care Clearinghouse |
|---|---|---|
Clinics | Health insurance companies | Entities that process nonstandard health information they receive from another entity into a standard (i.e., standard electronic format or data content), or vice versa. |
Doctors | Health maintenance organizations | |
Pharmacies | Company health plans | |
Nursing Homes | Government programs that pay for health care, such as Medicare, Medicaid, and the military and veterans health care programs | |
Psychologists | ||
Dentists | ||
Chiropractors |
- but only if they transfer any protected health information in an electronic form in connection with a transaction for which the United States Department of Health & Human Services (HHS) has adopted a standard. The list isn't exhaustive.
You can also use this tool by the Centers for Medicare & Medicaid Services to check whether you’re a covered entity or not.
A business associate is an organization or a person that provides certain services for a covered entity, involving the disclosure or use of protected health information.
You can check this short video to get a better understanding of the concept:
The Privacy Rule lists some of the activities and services that make an organization or person a business associate. It includes but not limited to billing, data analysis, consulting, quality assurance, claims processing and administration, etc.
A few real-life cases may look as follows:
- A pharmacy benefits manager that manages a health plan’s pharmacist network.
- An independent medical transcriptionist that provides transcription services to a physician.
- A third-party administrator that assists a health plan with claims processing.
If a business associate helps a covered entity carry out its healthcare functions and activities, it must have a written contract in which it’s specified what the business associate has been engaged to do.
At the same time, HIPAA isn’t applicable to businesses that may still deal with health information but are neither covered entities nor business associates. To name a few examples:
- gyms and fitness clubs;
- many mobile apps used for health and fitness purposes;
- those who conduct screenings at pharmacies, shopping centers, health fairs, or other public places for blood pressure, cholesterol, spinal alignment, and other conditions.
More details on business associates, contracts, and exceptions can be found at the HHS’s website.
Finally, the Federal Trade Commission has an interactive tool to define whether your mobile app is subject to key data protection federal laws — HIPAA, FD&C Act, and FTC Act. You can check it out here.
👮♂️ What Are the Consequences of the GDPR, PIPEDA, and HIPAA Violation?
Now you have a better understanding of what regulations may apply to your business. But what are the possible consequences of not complying with them? We hope you never learn it on your own experience so let’s take a look at the regulations themselves and real-life cases.
Fines for GDPR breaches 💶
Fines for failing GDPR IT compliance and data breach are one of the biggest compared to other similar regulations.
According to Article 83, violators may be fined up to either €20 million or 4% of the annual global turnover of the preceding financial year (whichever is higher!).
It’s quite important to figure out how to comply with EU GDPR as the Union is quite strict disregarding the size or status of the violators. To name a few cases:
❗️ Violator | 💰 Fine Amount | 🔎 Reasons | |
|---|---|---|---|
🛩 British Airways | £183 million | Poor security of user data resulted in a web skimming attack that affected 500,000 customers. | |
🤖 Google LLC (twice) | 1️⃣ €600,000; | 1️⃣ Insufficient consent, control, and transparency over the processing of personal data for the purposes of behavioral advertising; | |
🏦 UniCredit Bank Romania | €130,000 | Failed to implement required organizational and technical measures. | |
🛍 Unnamed online retailer | €7,000 | Nonconformity with users’ rights to erasure, and non-cooperation with the supervisory authority. | |
As you can see, failing to meet the GDPR compliance requirements can hit anyone: from global non-EU companies like Google to small online retailers.
Penalties for PIPEDA non-compliance 💵
Organizations that don’t comply with PIPEDA or obstruct the authorities in the investigation of a complaint can be fined:
- up to C$10,000 — for an offense punishable on summary conviction;
- up to C$100,000 — for an indictable offense.
The Office of the Privacy Commissioner can also demand remedial measures and ongoing audits to ensure that the organization is PIPEDA-compliant.
HIPAA violation & breach fines 💸
There are 4 HIPAA violation penalty tiers based on the level of perceived negligence within the organization that led to the violation. The fines can range from $100 to $50,000 per violation or per record, with up to $1.5 million per year for each violation.
🔎 Violation type | 📒 Each violation | 🗂 Violations of an identical provision in a calendar year |
|---|---|---|
Individual didn’t know they violated HIPAA | 100 – $50,000 | $1,500,000 |
Reasonable cause and not willful neglect | $1,000 – $50,000 | |
Willful neglect but corrected | $10,000 – $50,000 | |
Willful neglect and isn’t corrected | $50,000 | |
Talking about a few real-life cases:
- In September 2020, the Premera Blue Cross health insurer paid $6.85 million due to a breach affecting over 10.4 million people.
- In July 2020, Lifespan agreed to pay $1,040,000 as a result of an unencrypted stolen laptop breach.
- In May 2019, MIE paid $100,000 and agreed to take corrective action in order to settle potential HIPAA violations. MIE is an Indiana company that provides software and electronic medical record services to healthcare providers.
In some cases, HIPAA violations may lead to criminal penalties. For example, for offenses with the intent to transfer, use, or sell personal health data for personal gain, commercial advantage, or malicious harm.
📖 GDPR, PIPEDA & HIPAA Compliance: Key Things to Know
Now as you know whether you’re subject to the mentioned regulations as well as possible penalties, let’s take a closer look at the documents that are relevant to you.
🇪🇺 GDPR
The GDPR stands for the General Data Protection Regulation. As we’ve mentioned earlier, this regulation was adopted by the European Union and affects all businesses and individuals that collect or process personal data of EU citizens.
{ rel="nofollow" .default-md}*)](https://cdn.sanity.io/images/ordgikwe/production/ed3a458f50b59890f31a21da11243aa3d5526256-1200x900.jpg?w=1200&h=900&auto=format)
The GDPR is a main EU regulation on data privacy (image by Desmoulin)
What is the GDPR compliance? Basically, it means 2 things:
- providing individuals with control over their personal data;
- improving the way businesses manage personal data of their customers.
The regulation itself can be found here. It consists of 99 articles and introduces new requirements that need special attention from your side. But let’s start with the basics!
📊 What’s the personal data under the GDPR?
We’ve already used the term “personal data” a few times but it’s important to clarify it.
The EU’s definition of the term is quite broad. As stated in Article 4, personal data is
any information relating to an identified or identifiable natural person.
If we translate it from legal into human language, it includes almost any user-related data, for example:
- name
- location data
- identification number
- phone number
- browsing history
- IP address
- and any other types of data that relate to the user's economic, social, cultural, physiological, mental, physical, or genetic identity.
According to the same article, procession of personal data is also used in its widest meaning: from collection and storage to use and erasure.
Key elements of the GDPR 📖
In this paragraph, we’ll review the key requirements for GDPR website compliance and GDPR app compliance. Actually, the requirements are the same disregarding the platform, operating system, business size or type and so on — that’s why it’s important to pay attention either way.
Principles 🤝
All the requirements for the GDPR IT compliance are based on 6 privacy principles from Chapter 2:
- Lawfulness, fairness, and transparency
- Purpose limitation
- Data minimization
- Accuracy
- Storage limitation
- Integrity and confidentiality.
Below you can see a brief overview of these concepts:
Let’s see what you should do to comply with these principles!
⚖️ Lawfulness, fairness, and transparency
This principle includes 3 sub-principles:
💡 Principle | 📜 Description | ✅ How to comply | ||
|---|---|---|---|---|
Lawfulness | It’s illegal to use personal data of EU citizens in any way unless you have a lawful basis. | You need to identify your lawful basis (use this list) and include it in your privacy policy. | ||
Fairness | You must process personal data in ways that won’t cause unreasonable negative consequences for users. | Make sure that the way you use personal data doesn’t create any field for situations that can lead to user’s moral, financial, or any other kind of damage. | ||
Transparency | You must clearly and explicitly explain how you’re going to process users’ personal data. | Your privacy policy should include information on why you need to process the data, how you’re going to do that, and the contact details of the responsible person(s). | ||
Let’s take a look at Uber Privacy Notice and see how compliance works in real life.
For example, Uber has clearly explained its legal basis for collecting and processing personal data in paragraph III.F — and that matches the Lawfulness principle:
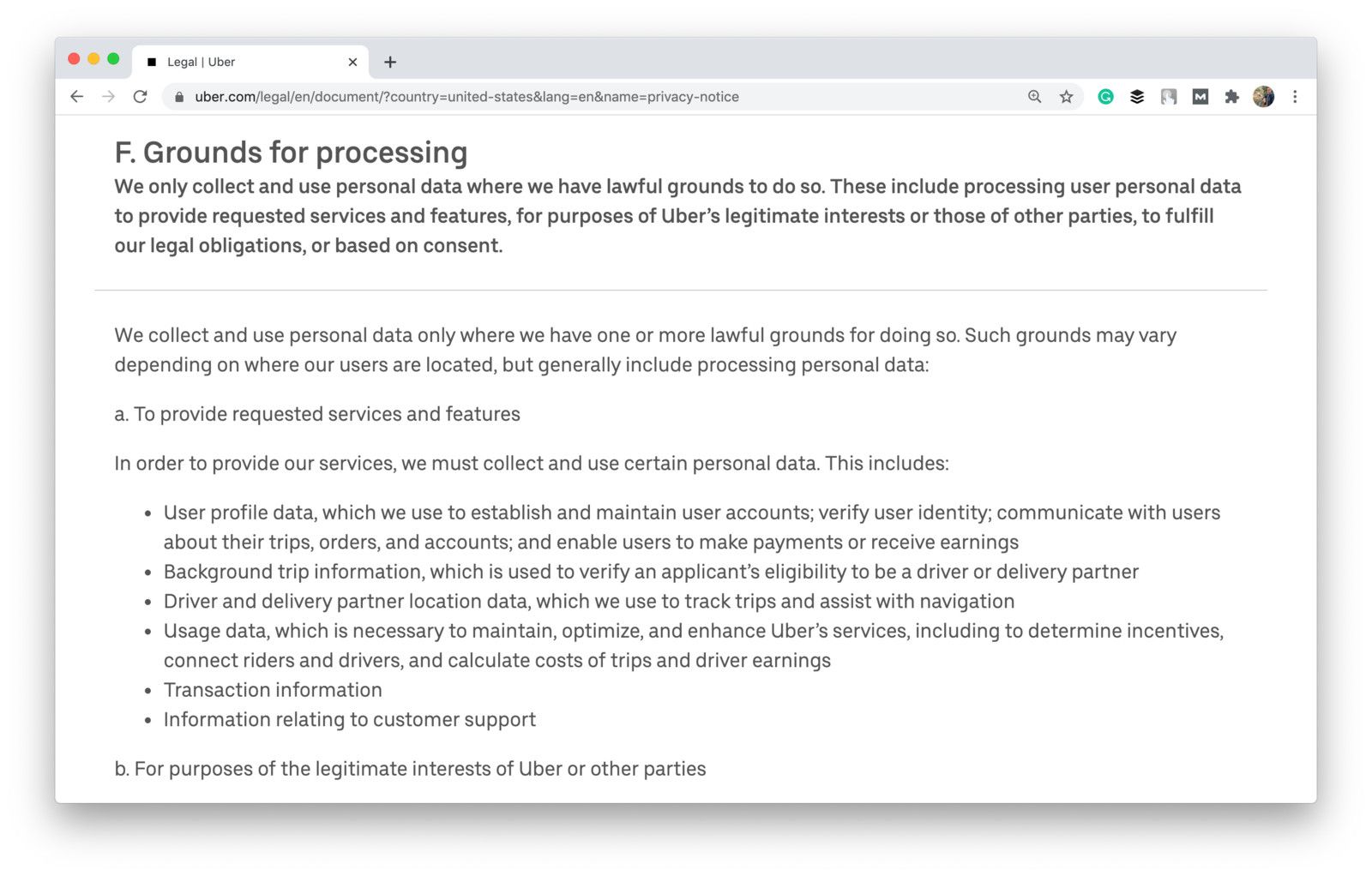
Shot from the Uber website
This privacy policy meets other requirements as well. The Transparency principle is covered in the following paragraphs:
- III.B ➡️ Why Uber needs to use personal data and how it uses such data
- II.B ➡️ entities responsible for data collection and procession
🔎 Purpose limitation
It’s not enough to notify users of what data you gather — you should also clearly explain how you’ll use it. The goal of this principle is to make sure that companies won’t use personal data in ways that haven’t been agreed with customers.
Thus, you should always have a relevant reason when asking for any kind of personal data. Pay attention, that the GDPR relates to all users’ personal data, not only your end customers.
Let’s say you represent an on-demand delivery platform. It means that you’re responsible not only for the personal data of your customers but couriers as well. What personal data and for what purposes can you ask your couriers?
- Personal identifiers like name and profile pic to display it to users.
- Contact details like email and phone number so your managers and customers can get in touch with couriers.
- Identity documents (ID or driving license) and biometric data (facial scans) to verify the courier’s identity and prevent fraud.
- Financial data like payment details for billing and invoicing.
- Location data to track the deliveries.
Stuart — one of leading Europe’s on-demand logistics platforms — puts purpose limitations in a nice table:
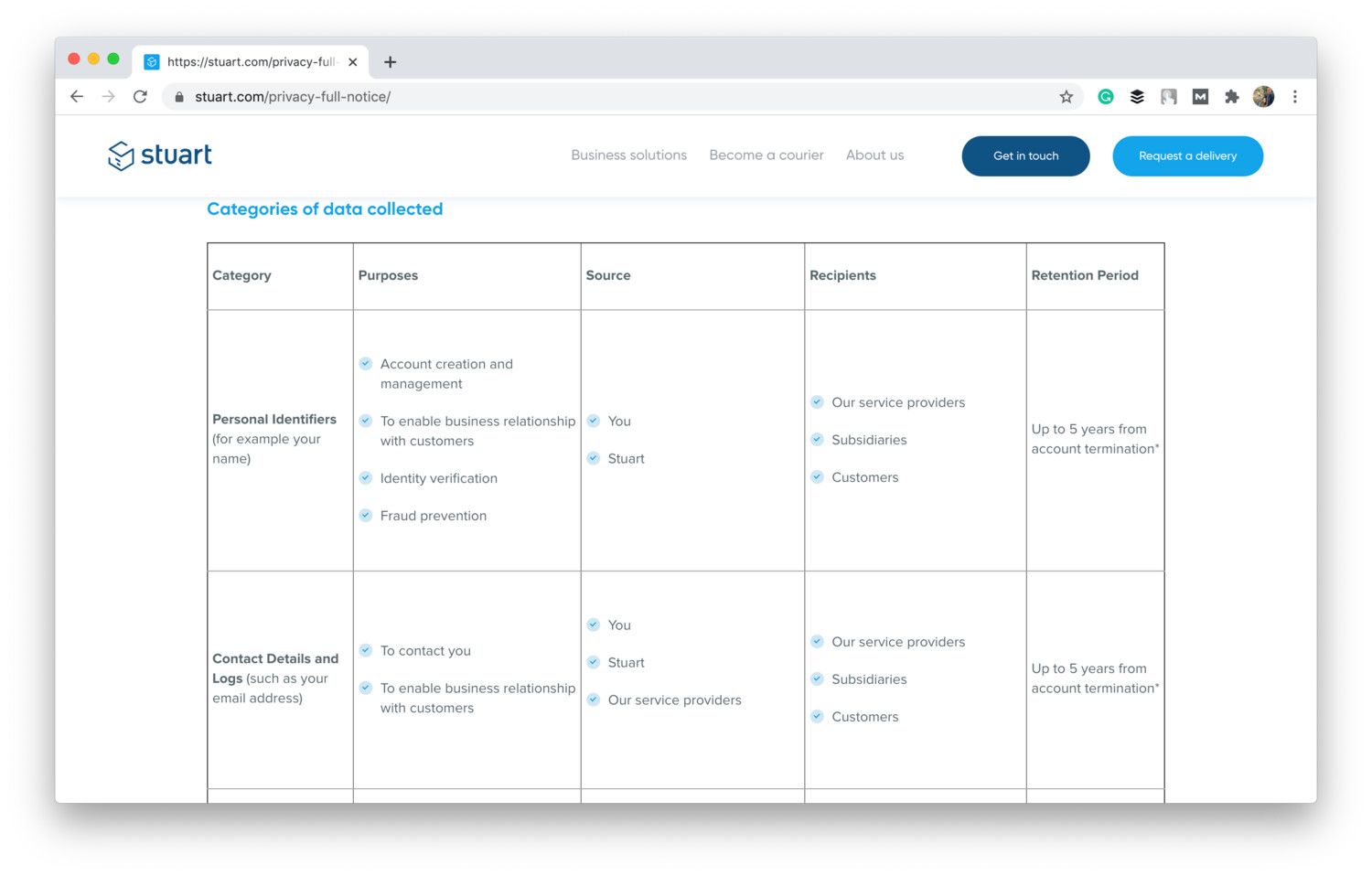
Shot from the Stuart website
At the same time, you shouldn’t use the mentioned data in any other way.
📲 Data minimization
The principle is quite simple: you must only ask for the personal data that is necessary to fulfill your purpose. In other words, you must process the minimum possible volume of personal data.
Purpose | ✅ Ok to ask | ❌ Not ok to ask | ||
|---|---|---|---|---|
Sign Up | Email/mobile phone number | ID photo (unless you provide services that imply age limitations or need to verify the identity of the user) | ||
Handling payments | Card number if you allow in-app payments | Card number if you allow cash-only payments | ||
Health Tracking | Medical records for the telemedicine platform | Medical records for the fitness tracking app that’s used to track calories and steps | ||
🎯 Accuracy
Data processors should also take steps to ensure data accuracy. It may be challenging if we’re talking about personal data submitted by the customers about themselves. Yet, there are still some steps you may take, in particular:
- Ensure that you record data accurately.
- Record the source of information.
- Add a special clause regarding data accuracy provided by users into your privacy policy. Note the importance of providing accurate information and the right of the user to update out-of-date or correct inaccurate personal information.
- If personal data turns out to be misleading, incorrect, or inaccurate, you should take all necessary steps to correct or erase it as quickly as possible.
💾 Storage limitation
The principle is quite simple: don’t store data any longer than necessary. The GDPR itself doesn’t specify the minimum or maximum storage period. Yet, what you should do is to document how long you’re storing data and justify the reason for this exact term.
Take a look at how GOV.UK provides a brief explanation of the storage period:
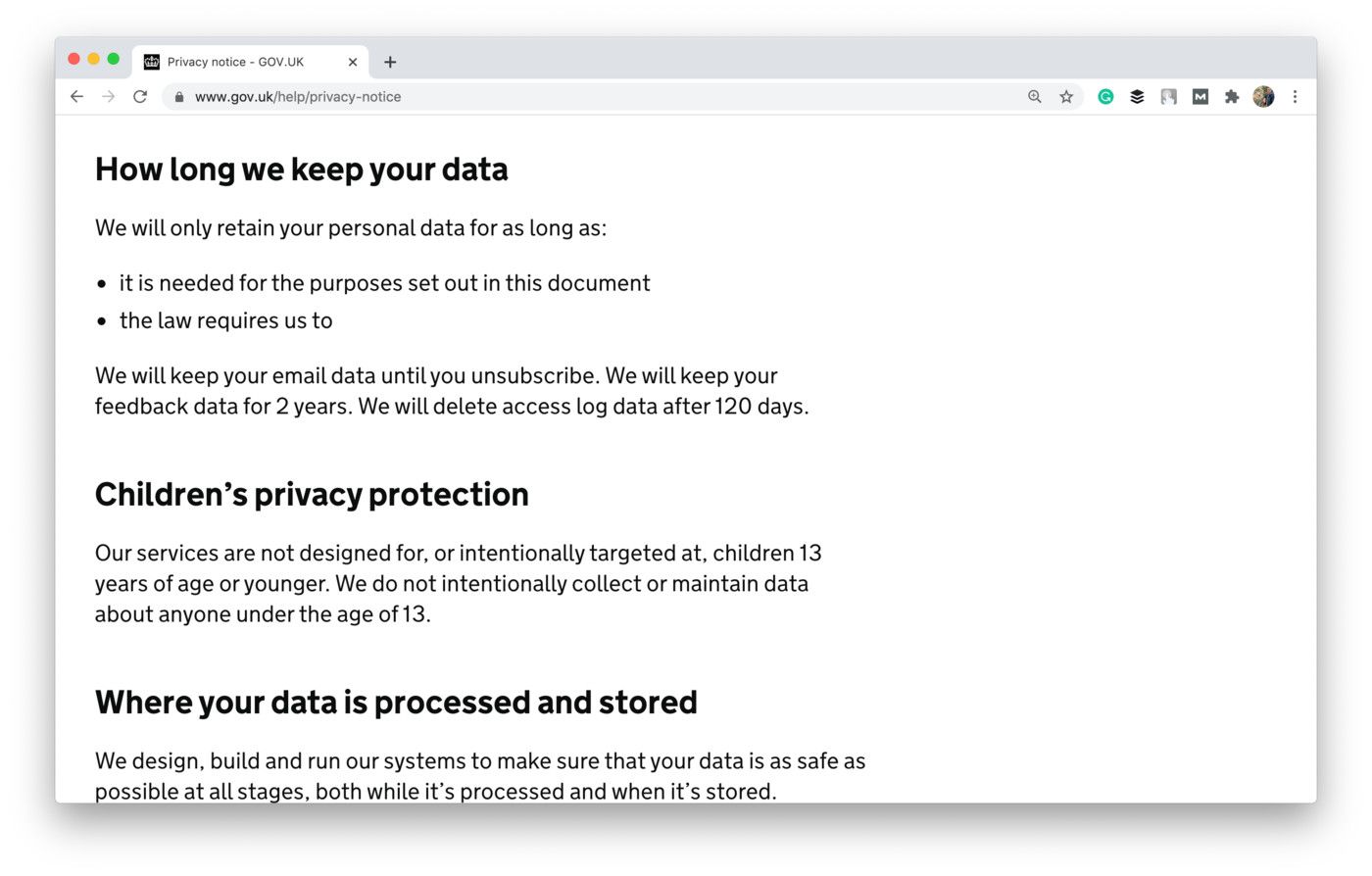
Shot from the GOV.UK website
🤫 Integrity and confidentiality
Finally, the last principle is quite obvious. It’s also known as the security principle and states that you must have appropriate security measures in place to prevent any possible damage to personal data.
However, the EU doesn’t specify what measures you should take. Actually, it’s your own responsibility since the Union is interested in keeping the data of its citizens safe while choosing the right means for it is up to you.
Many companies prefer to specify what security measures they take in their privacy policy. For example, this is how this principle is implemented in the privacy policy of Pandora, a radio app:
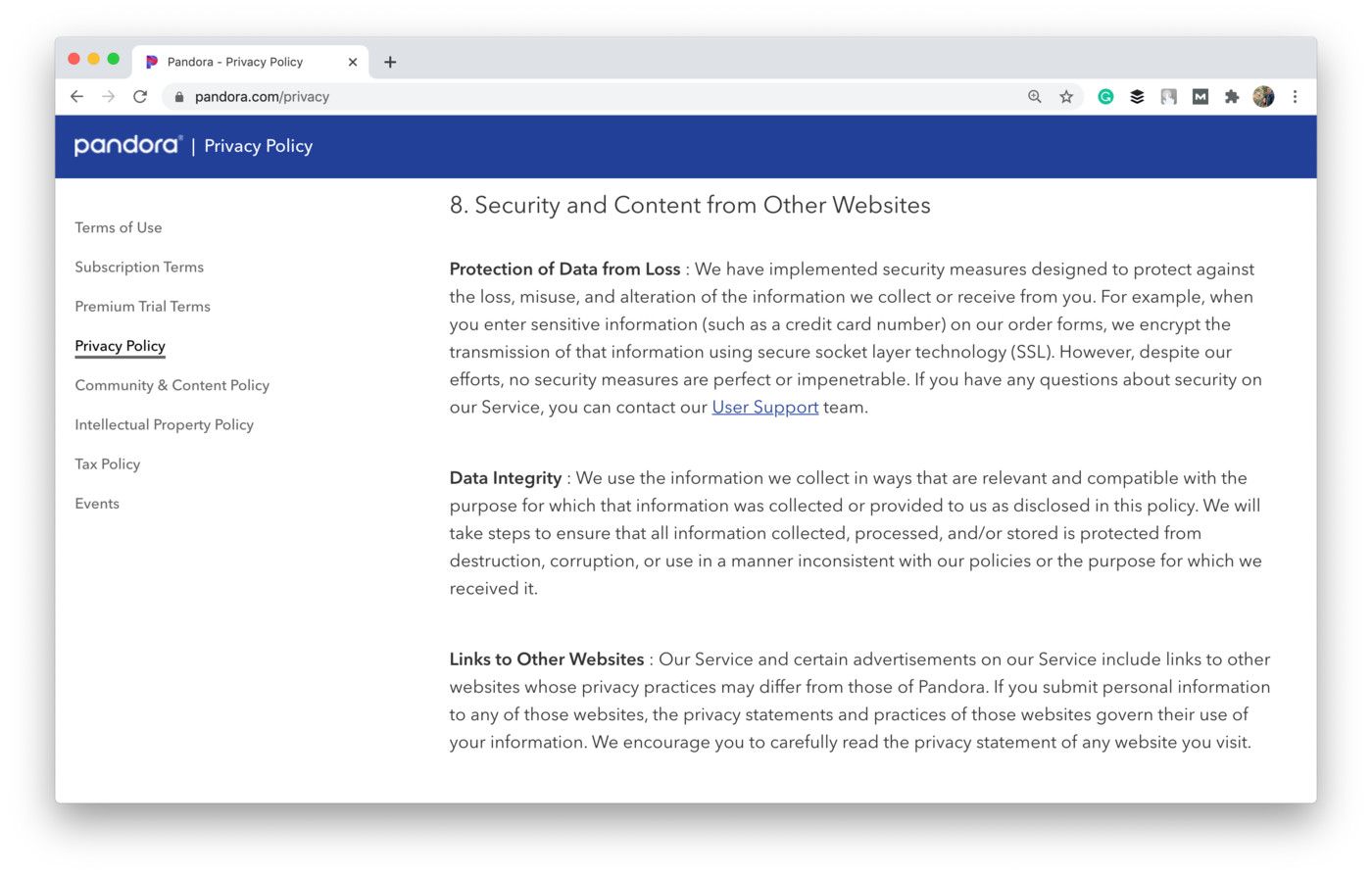
Shot from the Pandora website
Under this principle companies also should notify relevant supervisory authorities and affected users about data loss or breach within 72 hours.
Except for the principles, the GDPR Regulation introduces a few new privacy requirements and user rights. Let’s briefly review them, too!
🤝 Informed сonsent
The GDPR has also changed the old approach to acquiring the user’s consent for collecting and using his personal data. According to Recital 42, it must be active, informed, and acquired before you start processing personal data.
So as to achieve the GDPR app compliance with this rule, you must provide users with a possibility to give their direct consent to collect and use their data — for example, a checkbox or a button.
Yet, you can’t pre-tick such checkboxes or assume that continued use of your website or application means that active and informed consent.
Also, you must inform users on ways to withdraw their consent at any time.
Let’s compare how this rule is followed by two popular European low-cost airlines.
When signing up for Ryanair, they assume that “By signing up, you agree to Ryanair’s Privacy Policy and Terms of Use” without directly asking for the user’s consent.
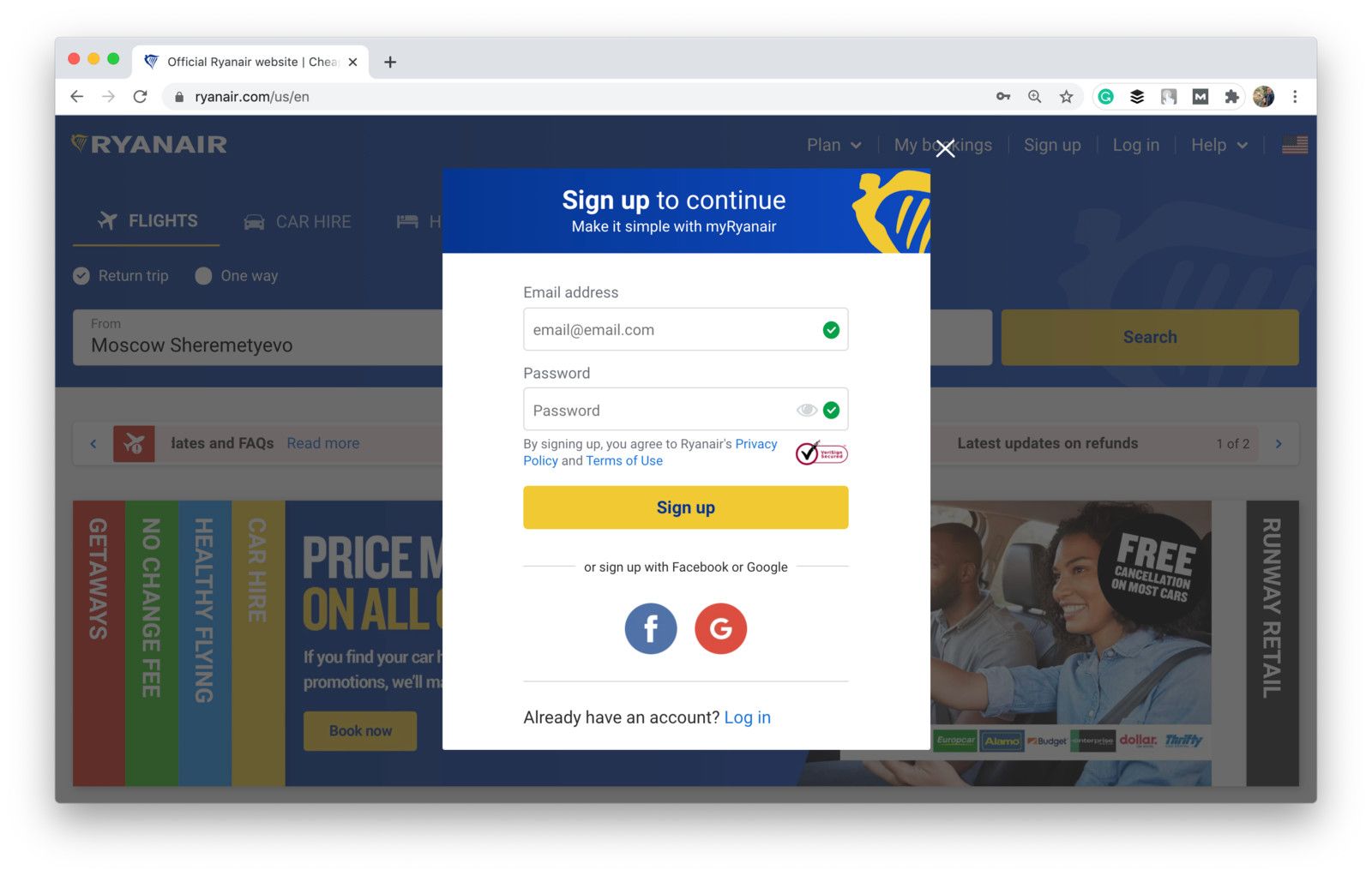
Shot from the Ryanair website
To sign up for Wizz Air, users have to provide their active consent by ticking checkboxes. Otherwise, they’ll be unable to proceed. Moreover, Wizz Air asks users’ consent for three separate purposes — to subscribe for a newsletter, to accept the Privacy Notice, and to agree to the Wizz Account Terms and Conditions.
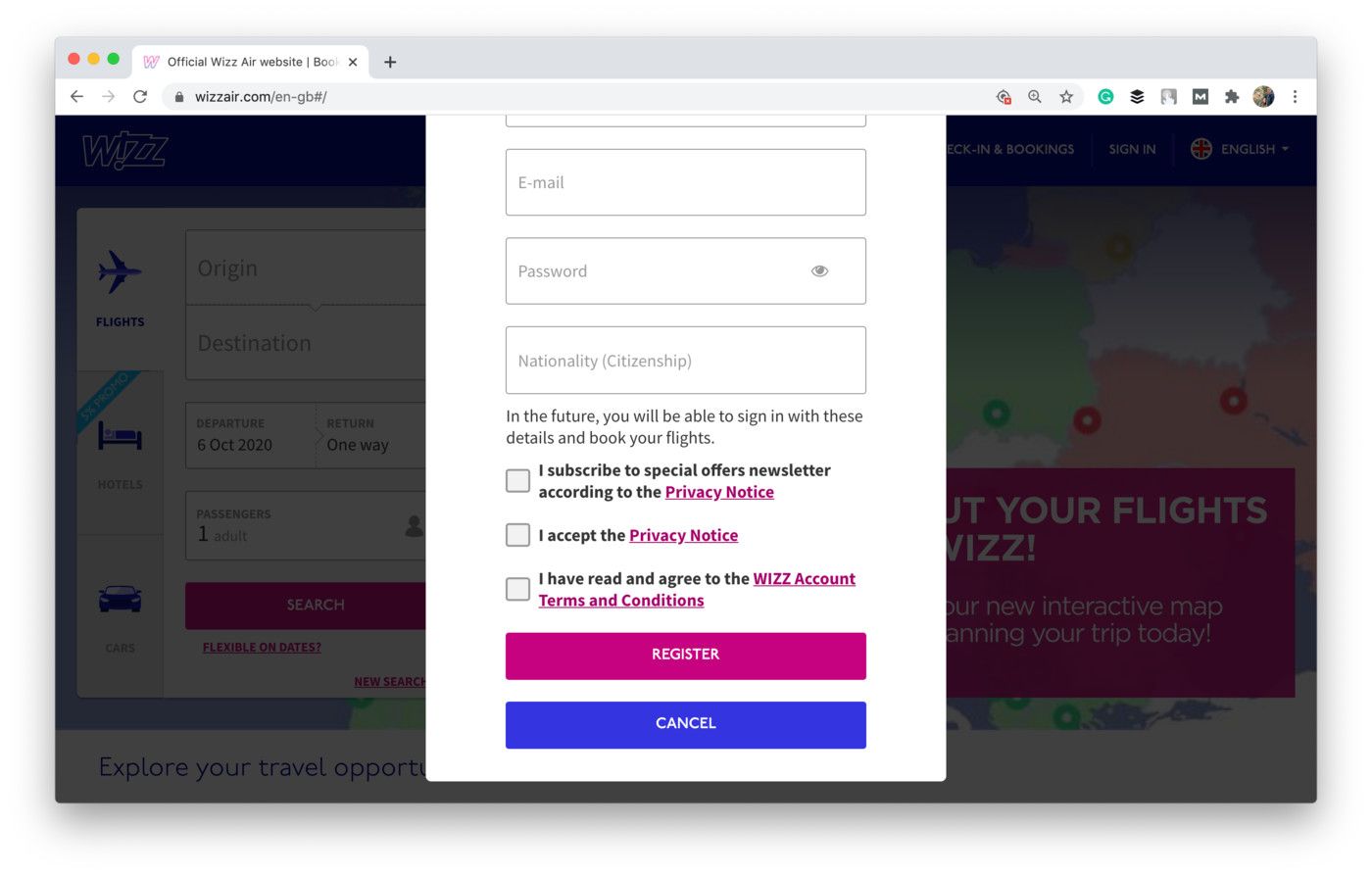
Shot from the Wizz Air website
This example seems far more GDPR compliant.
✅ Rights of users
Finally, to achieve the GDPR website compliance, you’ll need to take into account the rights of users introduced by the regulation. You can find them in Chapter 3 but we’ll briefly go over them in this article as well.
Right to access data 📩
If a user makes an information request on what of his personal data you store and process, you need to fulfill the request within 1 month. If the requested data is too complicated or too large, this period may be extended to 2 months.
You should also clearly describe how users can get a copy of their data or access it themselves in your privacy policy.
For example, Google has a separate page where users can request a copy of all personal data it has on them:
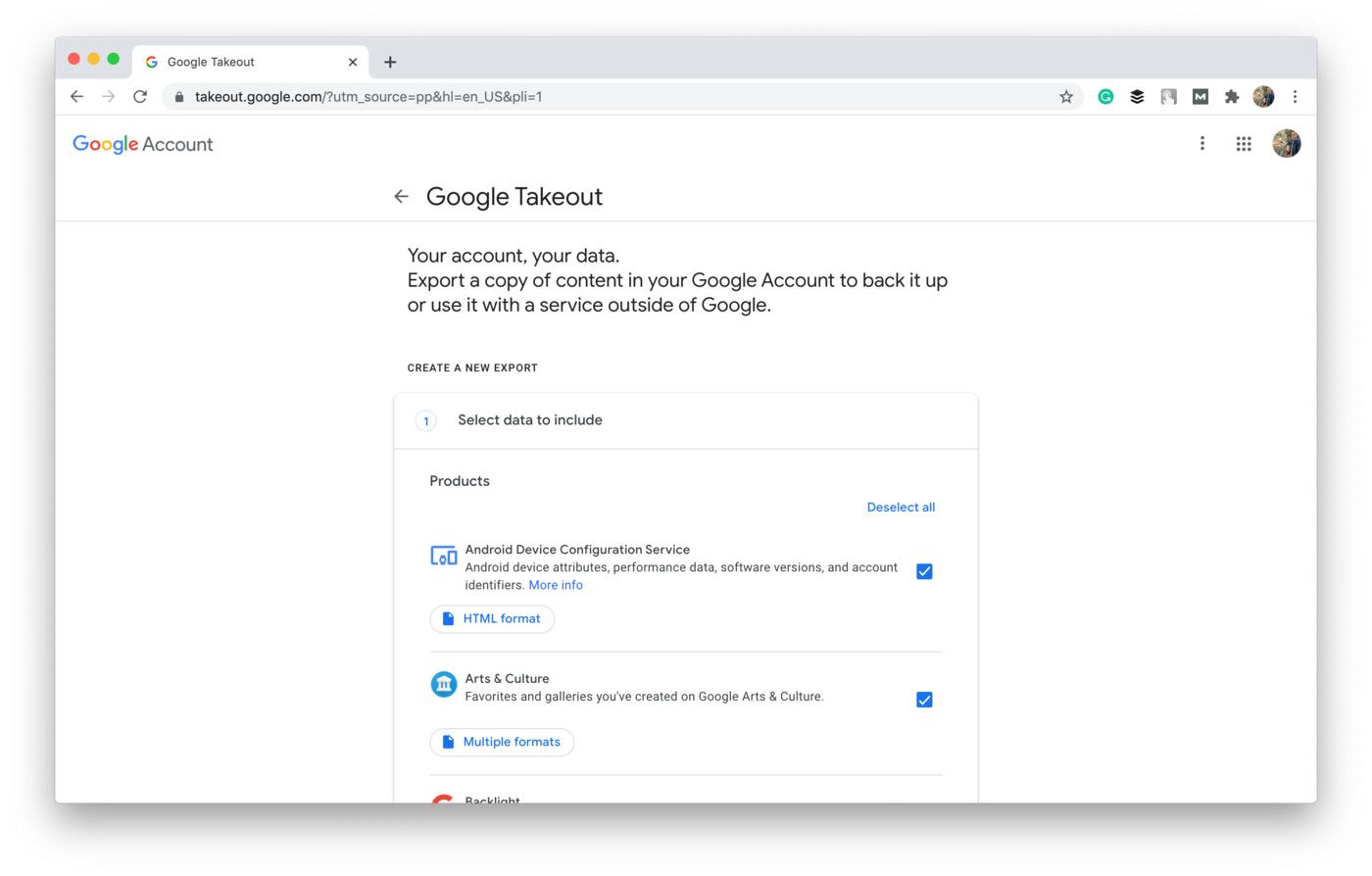
Shot from the Google Takeout website
Right to rectification 🔄
Users should have the right to change the data if it turns out to be incomplete, inaccurate, or out-of-date.
Where possible, provide users with the possibility to update their personal data in real-time and on their own, without spending your resources on this process.
Right to object ❌
The GDPR gives users the right to object to the processing of personal data at any time unless you provide “compelling legitimate grounds for the processing” which override this right.
In cases when personal data is processed for direct marketing purposes, you must immediately stop processing the data upon such a request.
Right to erasure (or the “Right to be forgotten”) 🧹
Under the GDPR, your website or mobile app users have the right to request the erasure of their personal data in case:
- it’s no longer necessary for initial purposes;
- the user withdraws consent for collecting and processing his personal data — and it was the only legal ground for the processing;
- user refers to his right to object;
- the data have been unlawfully processed;
- it’s needed for compliance with a legal obligation in Union or Member State law to which the user is subject.
Yet, Article 17 also names cases in which personal data shouldn’t be erased, so we recommend carefully checking the GDPR.
Take a look at how this right is implemented in the Spotify Privacy Policy:

Shot from the Spotify website
Right to restriction of processing 🔒
This right is somewhat similar to the right to erasure. Upon a user's request, you must immediately stop processing personal data (but not delete it!).
The GDPR specifies 4 lawful grounds for that:
- the user believes personal data to be inaccurate and waits until you verify it;
- the processing is unlawful but a user insists on restriction to use his personal data over its erasure;
- the data is no longer needs to be processed for initial purposes but shouldn’t be erased as a user needs it for establishment, exercise, or defense of legal claims;
- a user has used his right to object and waits for the solution.
Right to data portability 📲
Finally, users should be able to transmit their personal data to another app, website, or business without any interference from your side. It also means that you must provide his data in a structured, commonly used, and machine-readable format.
For example, Facebook offers its users to download their personal data in two popular formats: HTML and JSON.
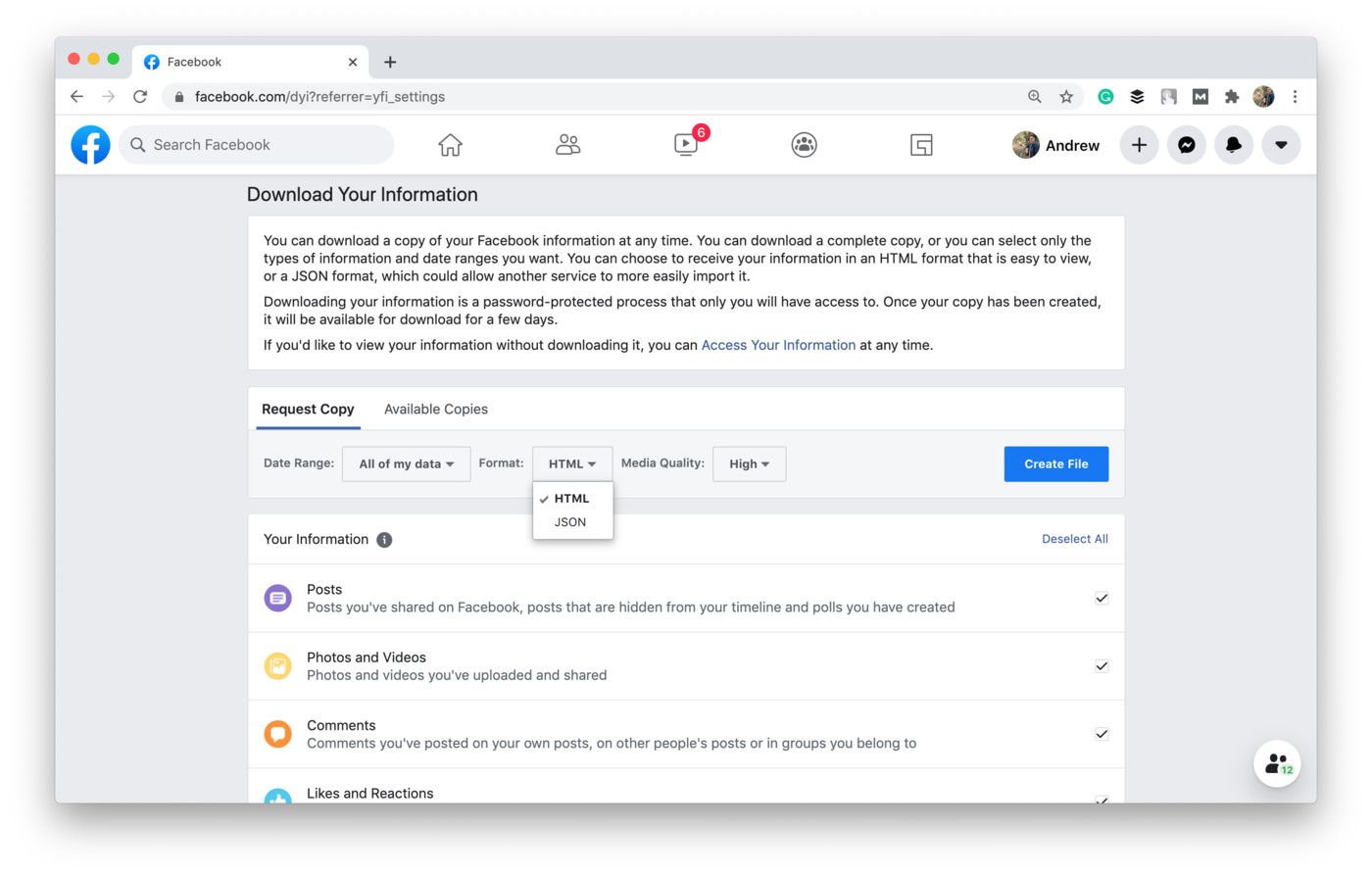
Shot from the Facebook website
📋 GDPR Compliance Checklist
We’ve also prepared a GDPR compliance checklist based on the mentioned principles. Here it is:
But now let’s move to another regulation — HIPAA.
🇺🇸 HIPAA
HIPAA stands for the Health Insurance Portability and Accountability Act that standardizes protected health information management in the U.S.
The document is noticeably bigger than GDPR. Moreover, it’s presented in a form of separate chapters and subchapters.
If you’d like to check the official version of the regulation, you should use this link (Parts 160, 162, and 164 of Subchapter C of Subtitle A of Title 45 of Code of Federal Regulations — what’s not to like about bureaucratic language 🙃).
{ rel="nofollow" .default-md}*)](https://cdn.sanity.io/images/ordgikwe/production/38f6b3d11ab7dd1266d85ab54c31711d2b0bcc8e-1600x1200.jpg?w=1600&h=1200&auto=format)
HIPAA is a key regulation to comply with for healthcare providers and businesses (image by Baten )
Alternatively, there is an unofficial version of HIPAA that presents the same standards in one document. It can be found here.
Before we move to the contents of HIPAA, let’s review what information it actually protects.
🧬 What information is covered under HIPAA?
Unlike GDPR that covers all types of personal information, HIPAA focuses on protected health information (PHI) — all "individually identifiable health information" that is transmitted or maintained in any format or medium. To understand the concept of the PHI, one should first take a look at the concept of health information.
Health information is any information that is received or created by a covered entity, school or university, life insurance company or employer, and relates to:
- treatment provided to a person;
- a person's past, present, or future mental/physical state or condition;
- past, present, or future payment for healthcare this person receives.
For example, it may be medical test results, prescriptions, diagnoses, and treatment information.
Yet, HIPAA considers as PHI only individually identifiable information that can be tied to a particular person. Thus, it should have at least one or more of the following 18 identifiers:
Type of identifiers | Identifiers | ||
|---|---|---|---|
👤 Basic Data |
| ||
☎️ Contact Details |
| ||
💊 Medical Data |
| ||
💰 Banking Data |
| ||
🚗 Driving-related Data |
| ||
💻 Technical Data |
| ||
🧬 Biometric data |
| ||
📋 Other Data |
| ||
The health data without these identifiers (if they’re initially missing or removed on purpose) is considered de-identified and can’t be subject to HIPAA.
PHI relates to a person's medical records, payments, treatments, and health conditions (past, present, and future) that are linked to individually identifiable information and can be used to identify a specific person.
Also, notice that PHI relates only to the personal data of health plan members and patients. Yet, it doesn’t include information from employment or educational records.
Key elements of HIPAA 📕
HIPAA compliance actually means compliance with its 5 main Rules — U.S. standards for collecting, transferring, storing, and using PHI. These rules make up the core of the regulation:
- Privacy Rule
- Security Rule
- Breach Notification Rule
- Enforcement Rule
- Patient Safety Rule
Let’s briefly review them!
# 1: Privacy Rule 🗄
The Privacy Rule established a set of national standards for the protection of PHI. Its main goal is to protect sensitive health information and the privacy of people who seek care.
This Rule defines general principles of uses and disclosures of PHI. Thus, covered entities are allowed to use or disclose PHI only as the Privacy Rule requires or permits, or in the way the subject of PHI (a person or its representative) authorizes in writing.
The Rule clearly defines cases when you can use or disclose PHI without any additional person’s authorization. These are:
- To the person himself/herself.
- For treatment, health care operations, and payments.
- By asking the person and providing him or her with the opportunity to agree or object.
- Incident to an otherwise permitted disclosure and use.
- Benefit activities and public interest (e.g. in cases required by law, or to prevent a serious threat to safety or health, for researches and workers’ compensation).
- As a limited data set from which specified identifiers have been removed.
Take a look at example of how the Tend dental studio from New York specifies this rule in its privacy policy:
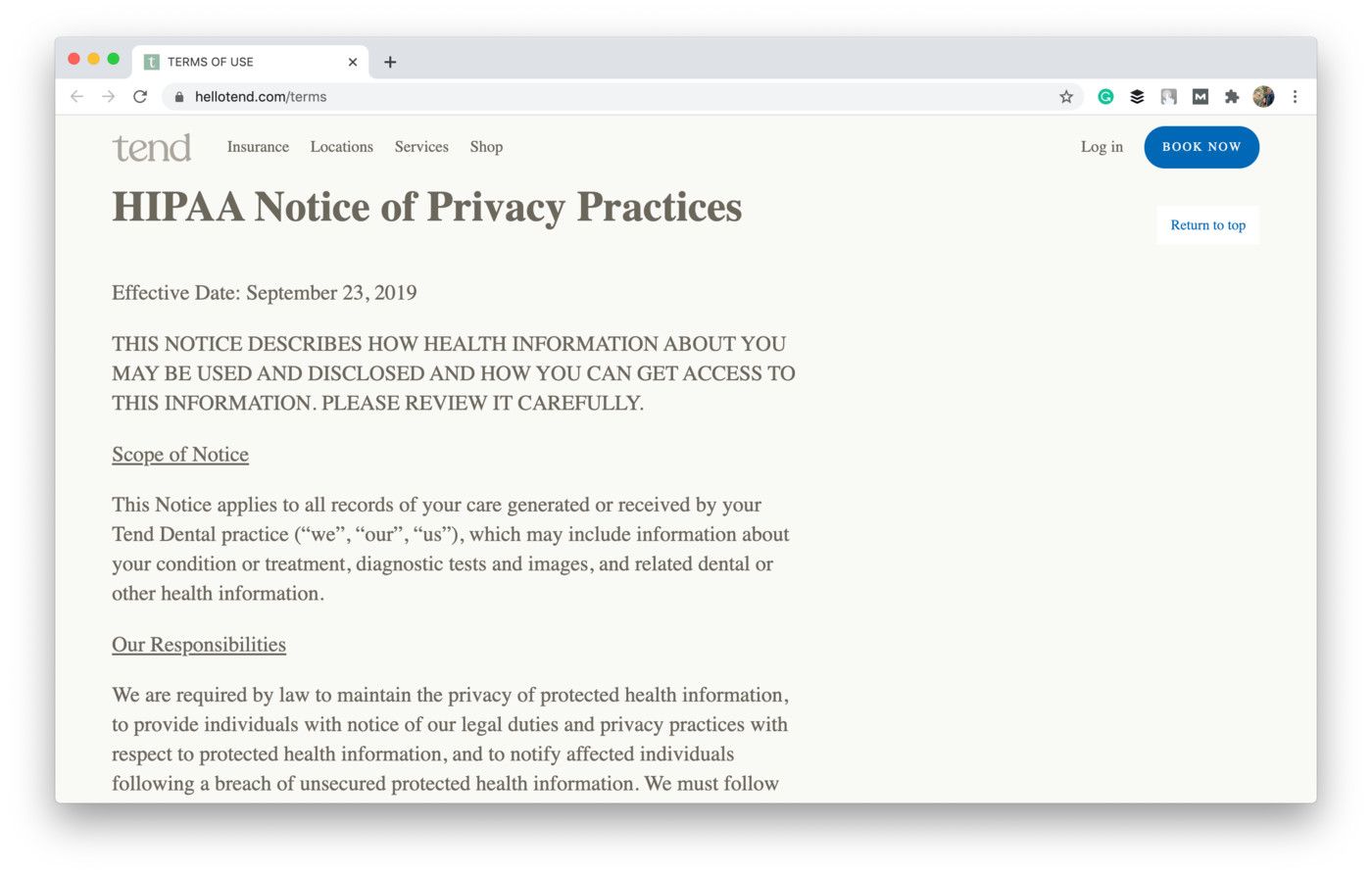
Shot from the Privacy Policy of Tend
The Rule also introduces a few following requirements:
- For use and disclosure in any other case except for the mentioned 6, you must get a person’s written authorization.
- You must ask for the minimum amount of PHI needed to accomplish your purpose.
- Covered entities must implement procedures, policies, and protocols for recurring requests for PHI disclosures
- Users should have the right to access, amend, restrict the use of their PHI.
More details on the Privacy Rule can be found on this HHS’s page.
# 2: Security Rule 🔒
The Security Rule addresses specific technical and non-technical safeguards that covered entities must put in place to comply with the Privacy Rule. Moreover, this Rule focuses specifically on electronic protected health information (e-PHI) which is the PHI that’s created, maintained, or transmitted in electronic form. Thus, this rule is the key to HIPAA website compliance and HIPAA app compliance.
The Security Rule implements administrative, physical, and technical safeguards for protecting e-PHI:
👩💼 Administrative Safeguards |
|---|
A covered entity should have a security official in charge who will be responsible for the development and implementation of security policies and protocols. |
🚪 Physical Safeguards |
Covered entities must **limit physical access **to its facilities, especially the ones from where e-PHI can be stolen. For that purpose, you may do something as complex as the implementation of specific security systems (e.g. video surveillance) to smaller steps like using better window and door locks. |
🤖 Technical Safeguards |
Covered entities must implement procedures that make it possible to access e-PHI only for authorized persons. You should also introduce technical measures to prevent unauthorized access. This will require the implementation of specific authentication features from password protection to biometric verification. |
More details on the Security Rule can be found on this HHS’s page.
# 3: Breach Notification Rule 📧
The regulation introduces specific measures to be taken in case of a breach. Moreover, under HIPAA there are 2 different protocols for cases when the breach affected fewer than 500 people and 500 or more people.
If it’s impossible to calculate the number of affected people for sure, the covered entity should provide an estimate and then apply the protocol that fits the situation.
For breaches with 500+ affected people, the covered entity must notify the Secretary of the breach and no later than 60 calendar days from the discovery of the breach.
For breaches affecting fewer than 500 people, the covered entity must notify the Secretary of the breach no later than within 60 days of the end of the calendar year in which the breach was discovered.
More details on the Breach Notification Rule as well as links for submitting breaches can be found on this HHS’s page.
# 4: Enforcement Rule 👨⚖️
This rule outlines the procedures that take place when the covered entity is investigated as a possible HIPAA violator.
We won’t focus on that as it’s not what you need to become HIPAA-compliant. If needed, more details on the Enforcement Rule can be found on this HHS’s page.
# 5: Patient Safety Rule 😷
The Rule introduces a framework by which covered entities may voluntarily report information to Patient Safety Organizations (PSOs) for the aggregation and analysis of patient safety events. Such information must be provided on a confidential basis.
It doesn’t play any big role when we’re talking about app or web compliance with HIPAA so we won’t focus on this part either.
More details on the Patient Safety Rule can be found on this HHS’s page.
📋 HIPAA Compliance Checklist
If you’re looking for how to become HIPAA compliant, take a look at the checklist below:
{ rel="nofollow" .default-md}*)](https://cdn.sanity.io/images/ordgikwe/production/f3adaa300e28e13a3119a08316008f9ee3eff5cd-900x471.jpg?w=900&h=471&auto=format)
HIPAA compliance checklist (image by DNSstuff)
Finally, let’s check on what step you can take to become PIPEDA compliant — if that’s your case, too!
🇨🇦 PIPEDA
PIPEDA stands for the Personal Information Protection and Electronic Documents Act. This is a Canadian data privacy law, adopted in 2000. The regulation introduces a set of consumer privacy standards which makes this law more similar to GDPR than to HIPAA.
🔎 What personal data does PIPEDA protect?
Under PIPEDA, personal data is any factual or subjective information about an identifiable individual.
The definition is quite wide as it includes anything from a name, age, ethnicity, ID number and IP addresses to such things as employee files, medical or credit records, and even opinions, comments, and disciplinary actions.
Thus, it doesn’t matter that much what kind of a website or mobile application you’re building — most likely you’ll collect some information that can be recognized as personal data.
Note that PIPEDA has its own exceptions. Examples of sensitive data not covered by the regulation are:
- info processed by federal government entities listed under the Privacy Act;
- business-related contact details (name, title, email, address, phone number, etc.) that are used solely for communication in relation to their profession or employment;
- information gathered solely for personal purposes (e.g. personal greeting card list);
- information gathered solely for literary, journalistic, or artistic purposes.
Key elements of PIPEDA 📙
Canadian regulation consists of 10 principles that make up the core of the document. In this paragraph, we’ll briefly review them and highlight key things you should consider to be PIPEDA-compliant.
The principles are somewhat similar to GDPR ones:
- Accountability.
- Purpose.
- Consent.
- Limitations.
- Duration.
- Accuracy.
- Protection.
- Transparency.
- Access.
- Challenge.
Also, you can check the full document by following this link.
# 1: Accountability 🤝
The first principle requires organizations to comply with all 10 PIPEDA principles. It means that you must:
- Develop privacy policies and procedures and implement all necessary practices to protect personal data.
- Appoint a data protection officer or another person who’ll be in charge of your website or app PIPEDA compliance.
Your privacy management program should be available to both employees and customers: for example, on your website, within the app, or in a downloadable format.
Finally, don’t forget to regularly review the program and update it. Especially when you introduce new technologies and initiatives that relate to personal data management.
# 2: Identifying Purposes 📲
This principle is similar to the one you can find in GDPR. It obliges organizations to explain the purposes for collecting and processing personal data to customers. The key requirement here is that your purpose must be clear and reasonable.
Here's how Zoom identifies its purposes for sharing personal data:
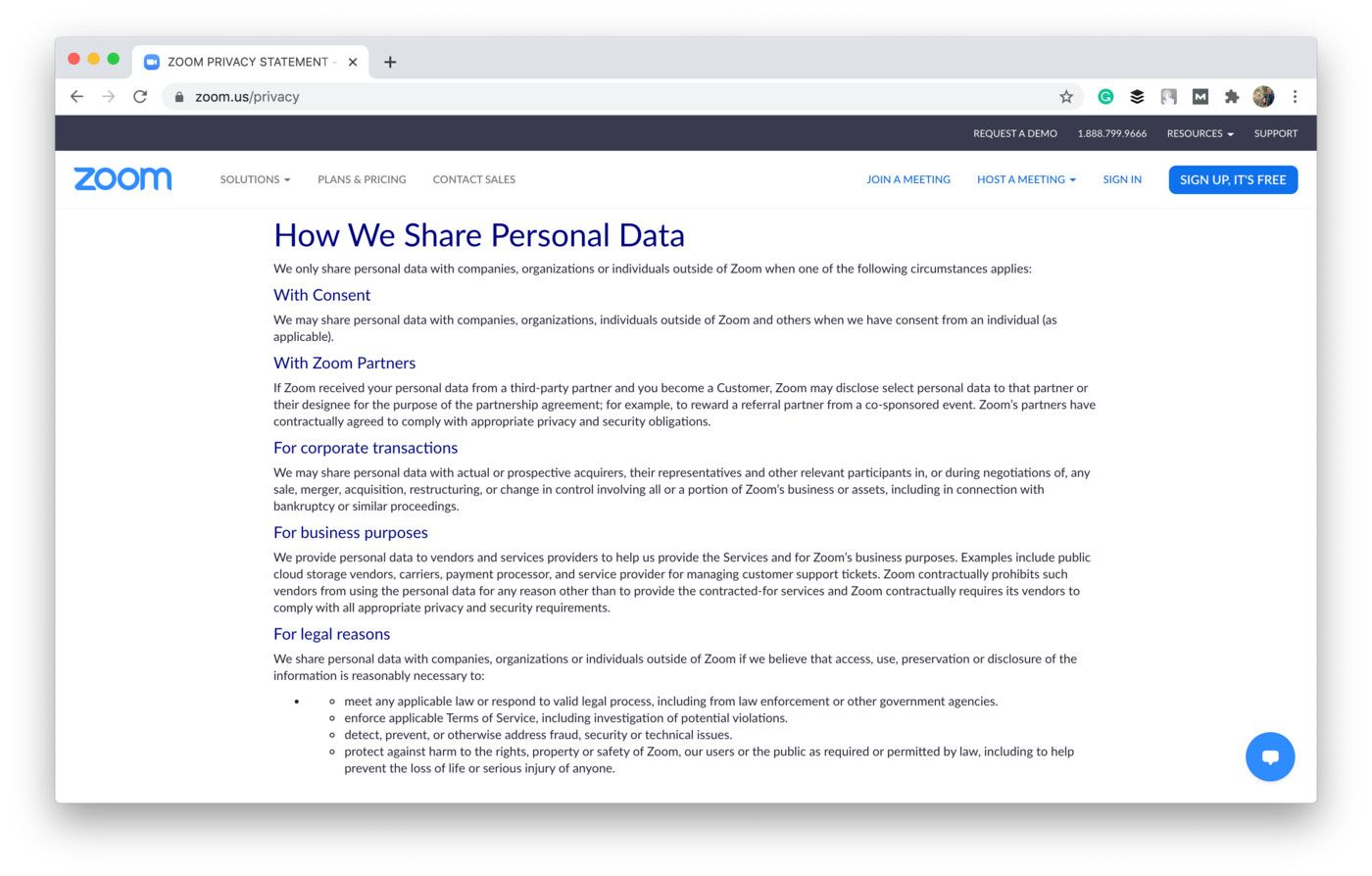
Shot from the Zoom website
Also note that if you change the purpose of gathering specific information, you’ll need to obtain new consent from your customers. The organization must keep a record of all consents and purposes, and be able to provide them in case of an investigation.
# 3: Consent ✅
It’s obvious that you should get prior consent before collecting or using the personal data of Canadian users. PIPEDA defines two forms of consent — express and implied.
Express is a more favorable form of consent so you should mostly rely on it. Also, organizations are required to ask for only express consent if:
- it authorizes the collection and processing of sensitive data;
- the purpose for the collection and processing may be outside of the reasonable expectations of the user;
- the collection and processing create a meaningful risk of significant harm.
You should also provide users with a right to withdraw their consent at any time, and with a right to proceed without consent for non-essential purposes (for example, if you’re collecting personal data solely for marketing purposes).
# 4: Limiting Collection 📥
To comply with this PIPEDA principle, organizations must ask only for the minimum necessary amount of personal data they need to process.
How do you find out whether it’s a minimum possible amount or not? You should be able to explain why you need this exact type of personal information.
Moreover, by asking only for the really necessary you lower the cost of storing, processing, and archiving the data as well as reduce the risk and
possible damage from breaches.
# 5: Limiting Use, Disclosure, and Retention ✅
PIPEDA allows organizations that work with users’ personal data to use or disclose it for 3 purposes:
- According to identified purposes.
- If a user consents to use it otherwise.
- To meet the law.
For example, memrise, a language learning app, specifices how exactly it will use personal data:
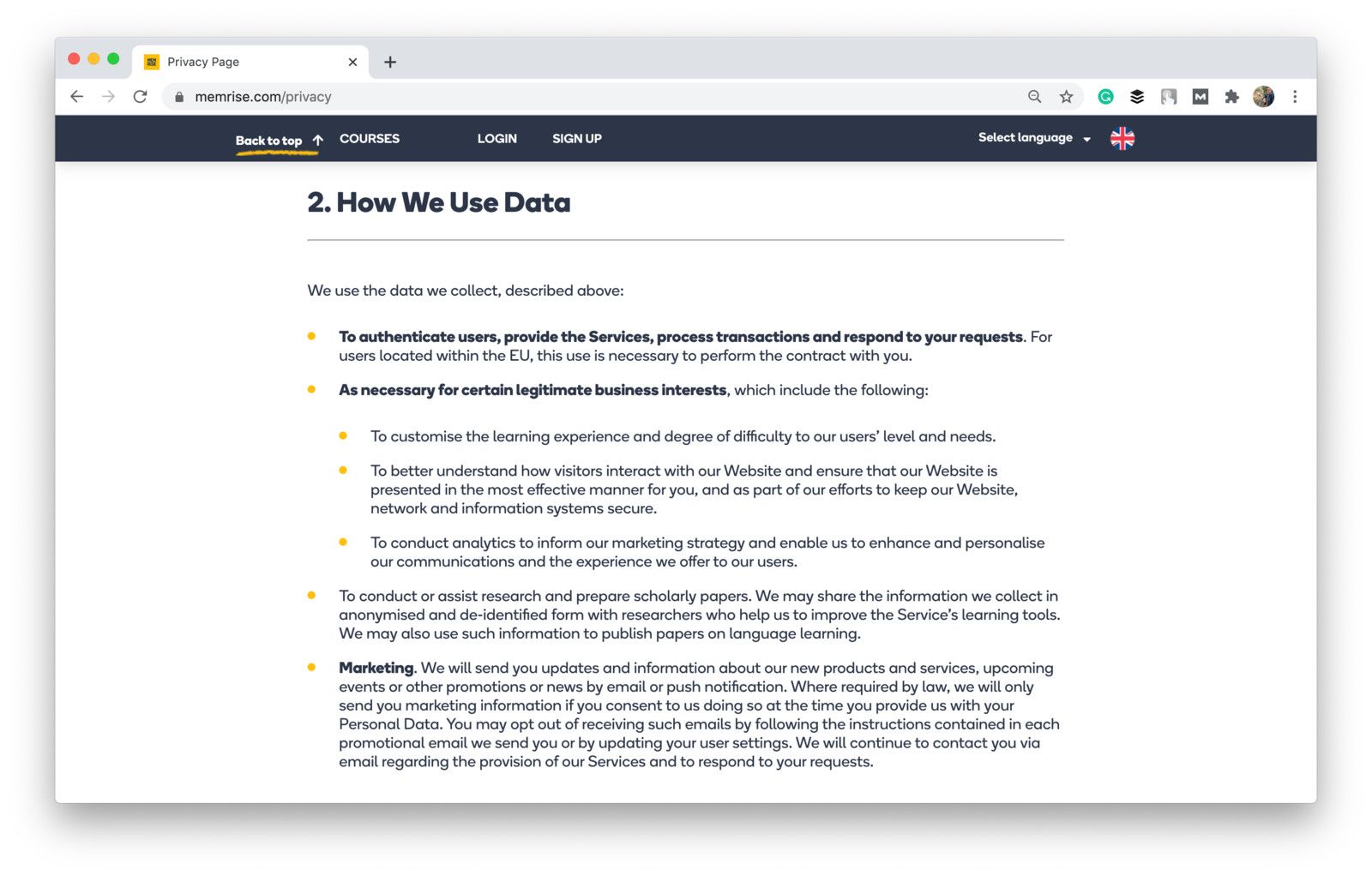
Shot from the Memrise website
You shouldn’t keep personal data for a longer period of time than you need it. You should also provide users and employees with guidelines for deleting and retaining such information. The regulation also suggests setting minimum and maximum retention periods.
# 6: Accuracy 🎯
Under PIPEDA, organizations must minimize the possibility of using out-of-date or incorrect personal information.
The Office of the Privacy Commissioner of Canada offers the following PIPEDA compliance checklist for this principle to keep the information accurate and double-check whether it needs any amendments:
🔲 Have a list of data that you use and specify those items that need the most attention.
🔲 Specify where this information can be found and how it can be accessed.
🔲 Always record the date when you first get or update personal data.
🔲 Have a protocol (set of steps and rules) on how you verify the accuracy of data.
🔲 Develop a schedule to review the information and keep it updated.
# 7: Safeguards 🔒
It’s your direct responsibility to keep personal data safe and protected against loss, theft, or any illegal access, disclosure, or use. Yet, PIPEDA doesn’t specify particular safeguards you should implement to comply — it’s up for you to choose as long as they’re efficient.
Yet, the regulation suggests to implement a 3-level security system similar to the one mentioned in the HIPAA’s Security Rule:
- Physical level includes measures like setting up an alarm system, locking filing cabinets, and installing a video surveillance system.
- Technological level requires taking steps like implementing encryption, protecting data with passwords, using firewalls, etc.
- Organizational level relates to administrative steps you can take: limit access to specific offices, organize security clearances, hold staff training, and so on.
# 8: Openness 🗃
Your policies and guidelines must be easily available and easily understandable. Avoid complex legal language as people need to be able to make an informed decision on whether to provide consent or not.
Pay special attention to the most important parts of your privacy policy: accountable data protection officer, users’ rights, types of information you collect and use, the legal basis for such actions, etc.
# 9: Individual Access 💻
Your users should have easy access to their personal data that you collect, store, and use. If needed, you must explain how you obtained, used, and disclosed it.
PIPEDA sets up a 30-day timeframe to answer such a request. In some cases you may use additional 30 days — but only if you can provide a reasonable explanation for the delay.
# 10: Challenging Compliance 👨⚖️
Finally, the organization should provide full support to a user even when he or she challenges its compliance with PIPEDA. In other words, you should explain to users how they can file a complaint, describe the investigation procedures, and inform on how they protect their data privacy rights with help from regulatory bodies.
Thus, you should have a person in charge who will handle complaints and investigations within the company.
You can also check this page by the Office of the Privacy Commissioner of Canada for more details on the mentioned PIPEDA principles. We’ve also prepared a PIPEDA compliance checklist — take a look!
📋 PIPEDA Compliance Checklist
Note that it’s not an exhaustive list of things you need to do to comply with PIPEDA. The aim of this checklist is to sum up the key ideas of PIPEDA’s principles and focus your attention on things that require the most attention.
💡 Takeaways
We hope now you know & understand more about how to comply with GDPR, PIPEDA, or HIPAA. Despite we highlighted all the key rules of these regulations in this article, we still strongly recommend either reaching out to experts in data privacy or carefully studying the original texts of regulations on your own.
But if you’re looking for a reliable Tech-Partner to support you with your Website or Mobile App Development — we’re here to help! Drop us a line by clicking a button below and we’ll see how we can contribute to your idea!

![Stormotion client Alexander Wolff, CPO from [object Object]](/static/a16ba3c9580effc3ab9a68d115eadffe/b0e74/alex.png)


